- [실습] 3. EKS IRSA & Pod Identitty - 실습2(Kubernetes Service Accounts)2024년 04월 14일
- yeongki0944
- 작성자
- 2024.04.14.:07
실습2 - Kubernetes Service Accounts
- Kubernetes Pods are given an identity through a Kubernetes concept called a Kubernetes Service Account.
- When a Service Account is created, a JWT token is automatically created as a Kubernetes Secret.
- This Secret can then be mounted into Pods and used by that Service Account to authenticate to the Kubernetes API Server.
# 파드2 생성 cat <<EOF | kubectl apply -f - apiVersion: v1 kind: Pod metadata: name: **eks-iam-test2** spec: containers: - name: my-aws-cli image: amazon/aws-cli:latest command: ['sleep', '36000'] restartPolicy: Never terminationGracePeriodSeconds: 0 EOF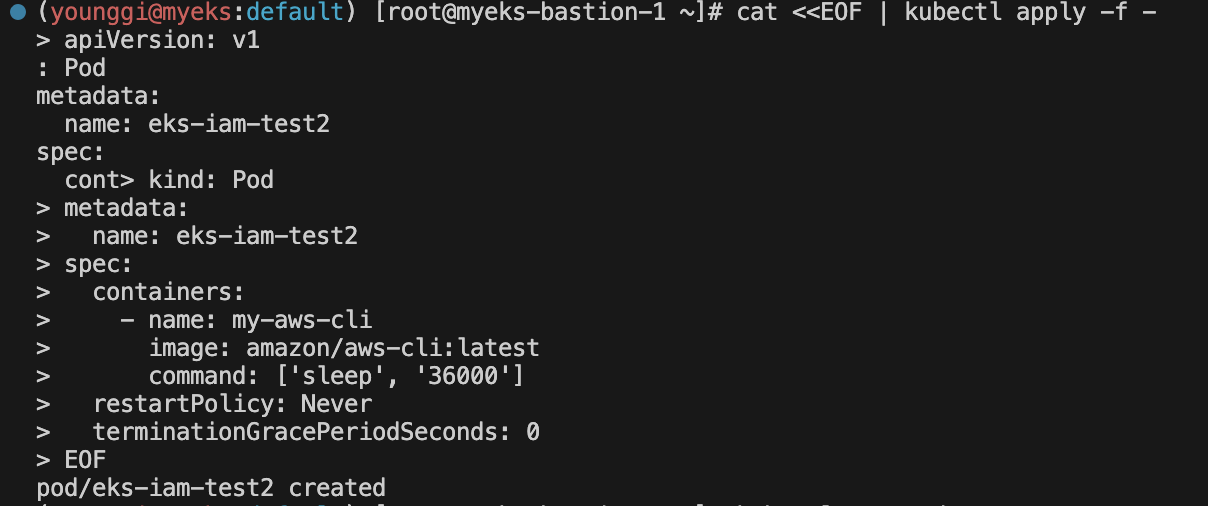
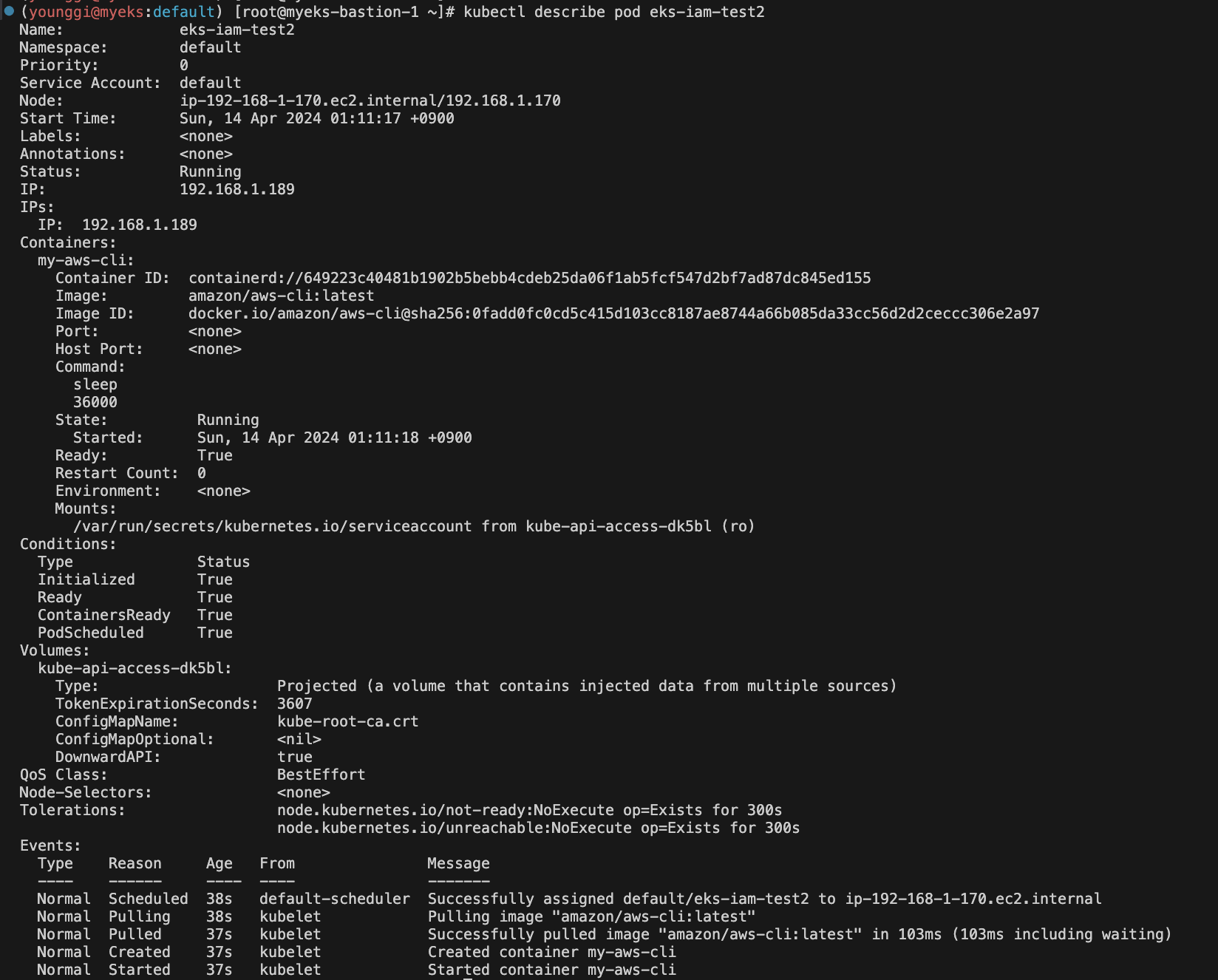
kubectl get pod kubectl describe pod
kubectl get pod eks-iam-test2 -o yaml | kubectl neat | yh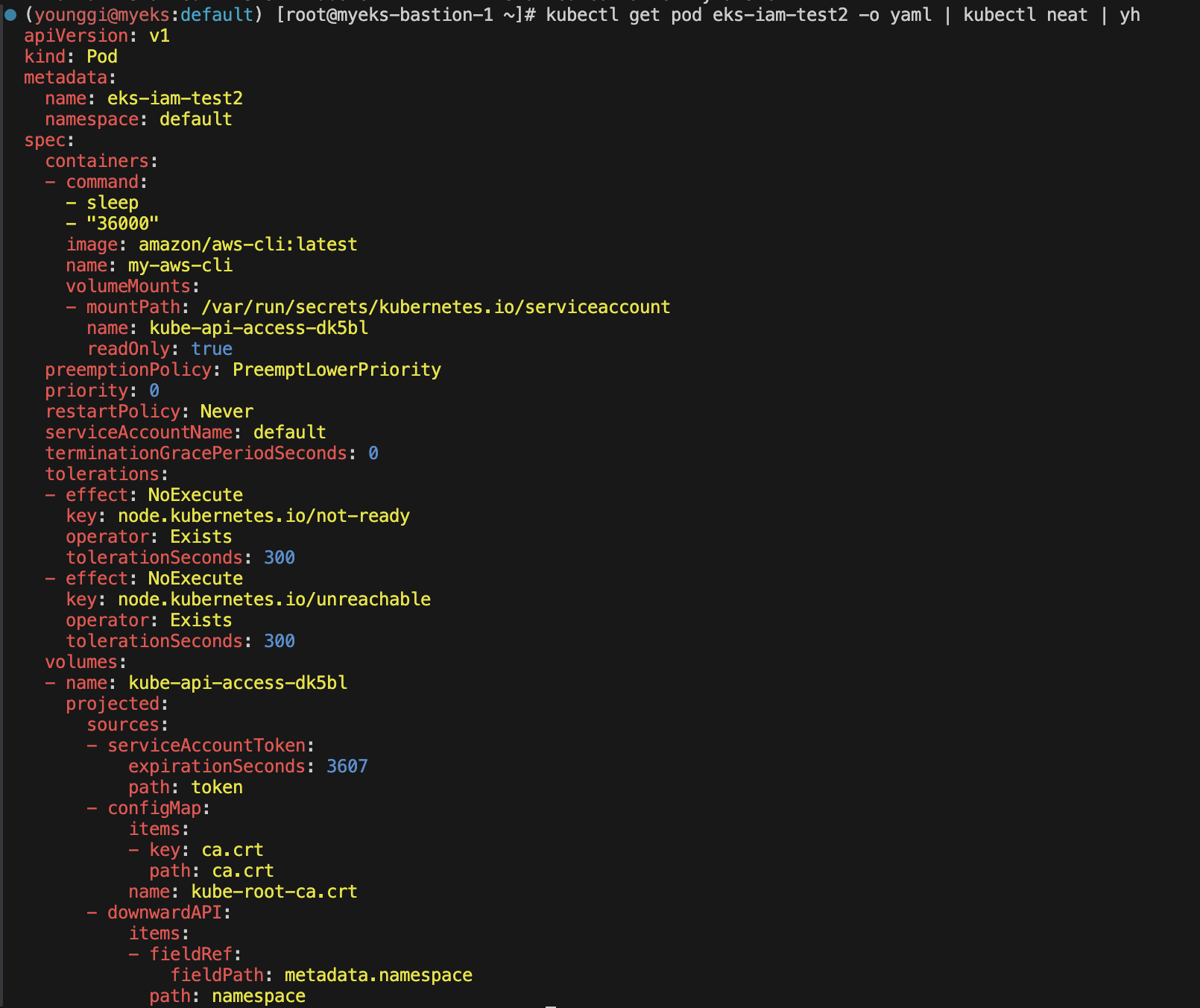
kubectl exec -it eks-iam-test2 -- ls /var/run/secrets/kubernetes.io/serviceaccount kubectl exec -it eks-iam-test2 -- cat /var/run/secrets/kubernetes.io/serviceaccount/token ;ech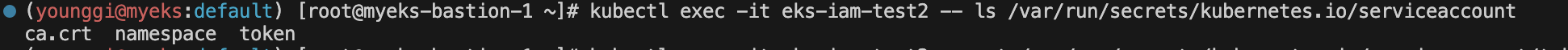

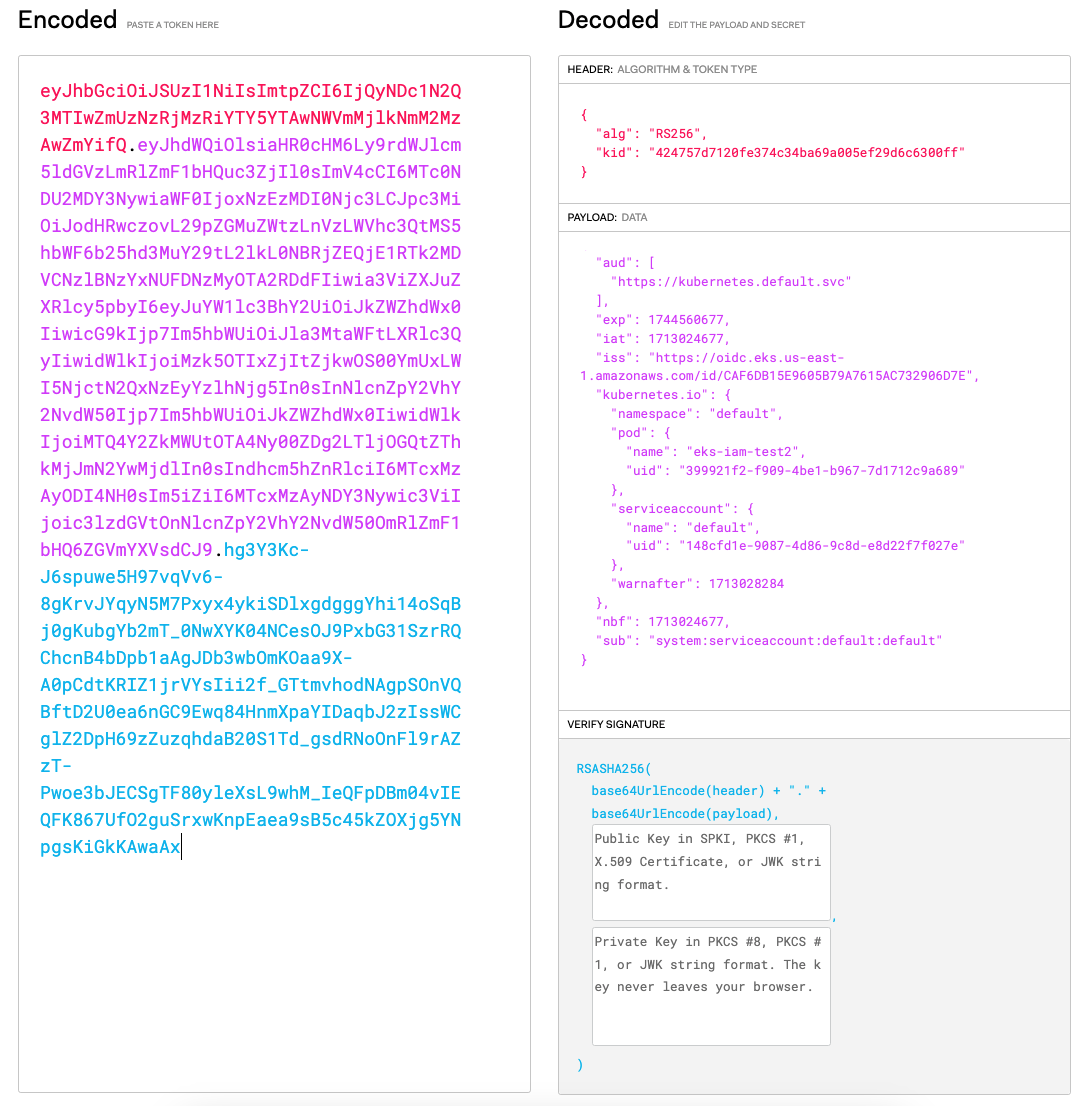
eyJhbGciOiJSUzI1NiIsImtpZCI6IjQyNDc1N2Q3MTIwZmUzNzRjMzRiYTY5YTAwNWVmMjlkNmM2MzAwZmYifQ.eyJhdWQiOlsiaHR0cHM6Ly9rdWJlcm5ldGVzLmRlZmF1bHQuc3ZjIl0sImV4cCI6MTc0NDU2MDY3NywiaWF0IjoxNzEzMDI0Njc3LCJpc3MiOiJodHRwczovL29pZGMuZWtzLnVzLWVhc3QtMS5hbWF6b25hd3MuY29tL2lkL0NBRjZEQjE1RTk2MDVCNzlBNzYxNUFDNzMyOTA2RDdFIiwia3ViZXJuZXRlcy5pbyI6eyJuYW1lc3BhY2UiOiJkZWZhdWx0IiwicG9kIjp7Im5hbWUiOiJla3MtaWFtLXRlc3QyIiwidWlkIjoiMzk5OTIxZjItZjkwOS00YmUxLWI5NjctN2QxNzEyYzlhNjg5In0sInNlcnZpY2VhY2NvdW50Ijp7Im5hbWUiOiJkZWZhdWx0IiwidWlkIjoiMTQ4Y2ZkMWUtOTA4Ny00ZDg2LTljOGQtZThkMjJmN2YwMjdlIn0sIndhcm5hZnRlciI6MTcxMzAyODI4NH0sIm5iZiI6MTcxMzAyNDY3Nywic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50OmRlZmF1bHQ6ZGVmYXVsdCJ9.hg3Y3Kc-J6spuwe5H97vqVv6-8gKrvJYqyN5M7Pxyx4ykiSDlxgdgggYhi14oSqBj0gKubgYb2mT_0NwXYK04NCesOJ9PxbG31SzrRQChcnB4bDpb1aAgJDb3wbOmKOaa9X-A0pCdtKRIZ1jrVYsIii2f_GTtmvhodNAgpSOnVQBftD2U0ea6nGC9Ewq84HnmXpaYIDaqbJ2zIssWCglZ2DpH69zZuzqhdaB20S1Td_gsdRNoOnFl9rAZzT-Pwoe3bJECSgTF80yleXsL9whM_IeQFpDBm04vIEQFK867UfO2guSrxwKnpEaea9sB5c45kZOXjg5YNpgsKiGkKAwaA
# aws 서비스 사용 시도 kubectl exec -it eks-iam-test2 -- aws s3 ls
# 서비스 어카운트 토큰 확인 SA_TOKEN=$(kubectl exec -it eks-iam-test2 -- cat /var/run/secrets/kubernetes.io/serviceaccount/token) echo $SA_TOKEN
# 파드2 삭제 kubectl delete pod eks-iam-test2 다음글이전글이전 글이 없습니다.댓글
다음글이전글이전 글이 없습니다.댓글
스킨 업데이트 안내
현재 이용하고 계신 스킨의 버전보다 더 높은 최신 버전이 감지 되었습니다. 최신버전 스킨 파일을 다운로드 받을 수 있는 페이지로 이동하시겠습니까?
("아니오" 를 선택할 시 30일 동안 최신 버전이 감지되어도 모달 창이 표시되지 않습니다.)