- [실습] 2. EKS 인증/인가 - A deep dive into simplified Amazon EKS access management controls2024년 04월 13일
- yeongki0944
- 작성자
- 2024.04.13.:06
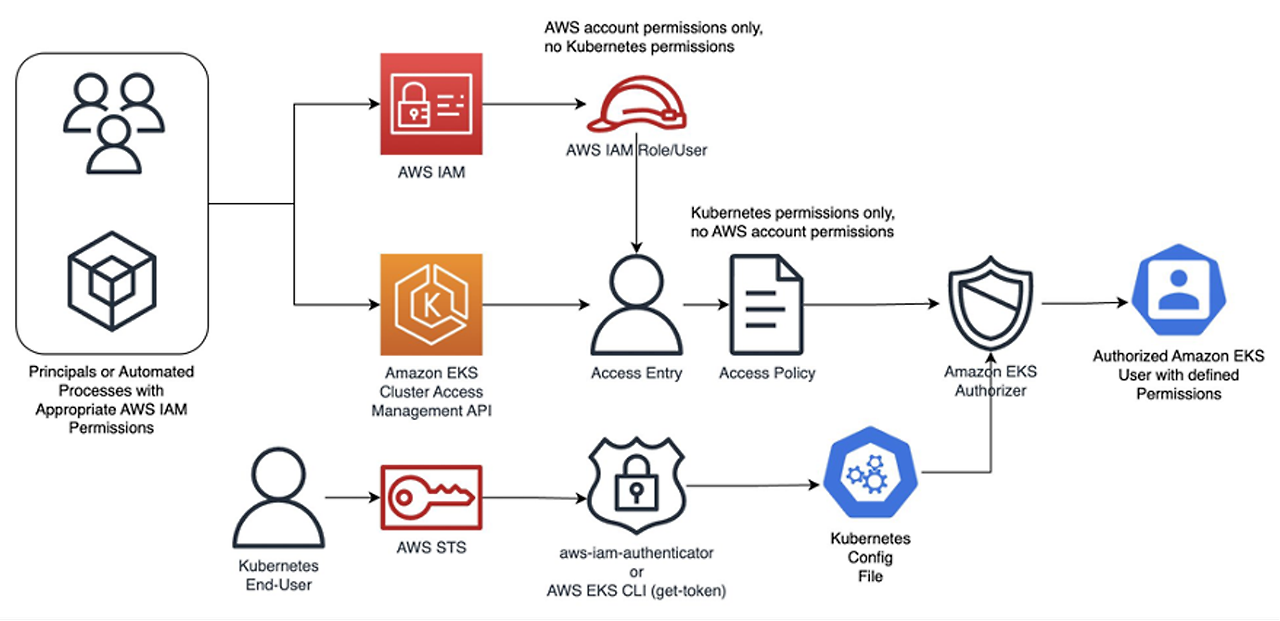
https://aws.amazon.com/blogs/containers/a-deep-dive-into-simplified-amazon-eks-access-management-controls/ - EKS → 액세스 구성 모드 확인 : EKS API 및 ConfigMap ← 정책 중복 시 EKS API 우선되며 ConfigMap은 무시됨

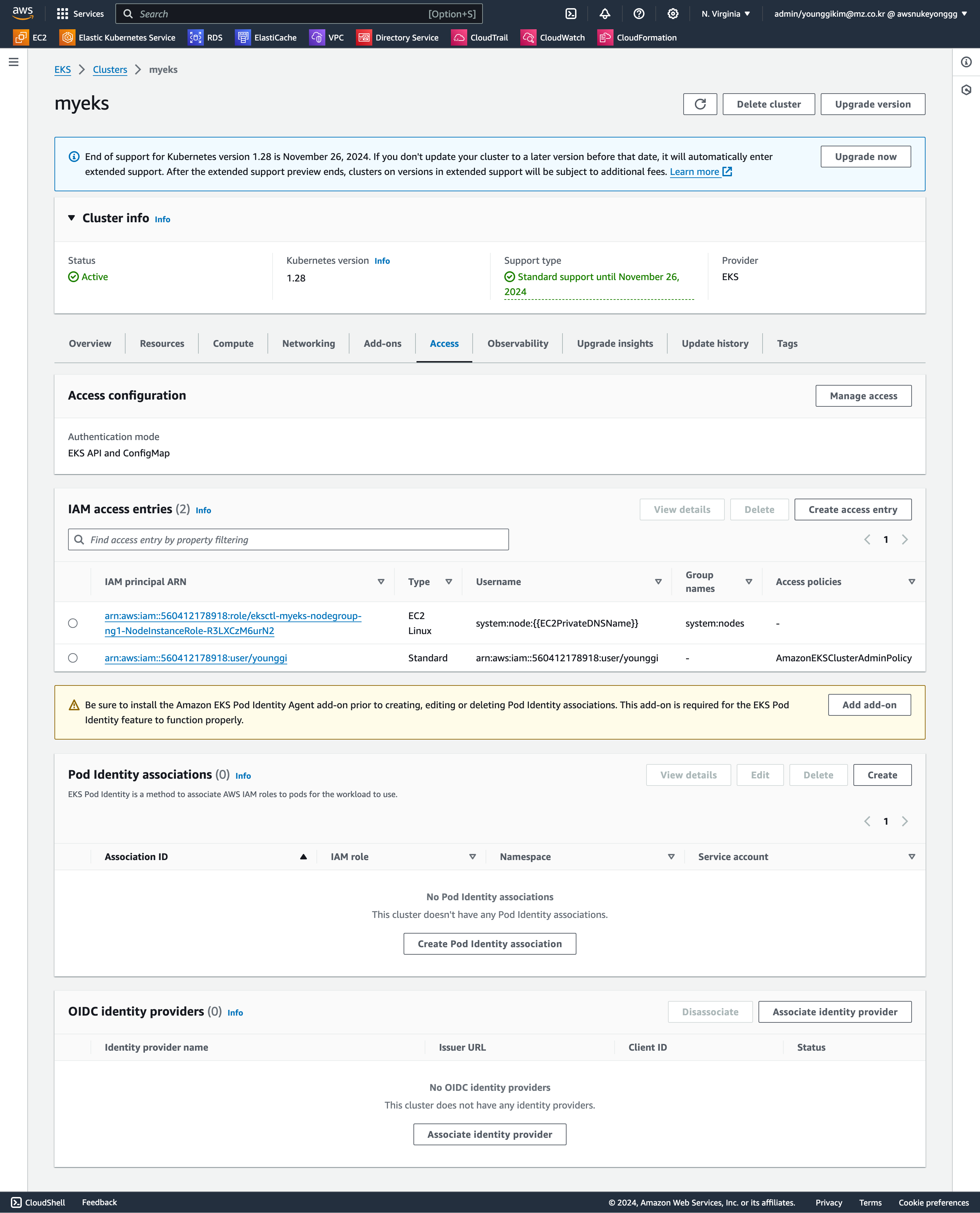
기본 정보 확인
- access policy, access entry, associated-access-policy - Link Docs User-facing_roles
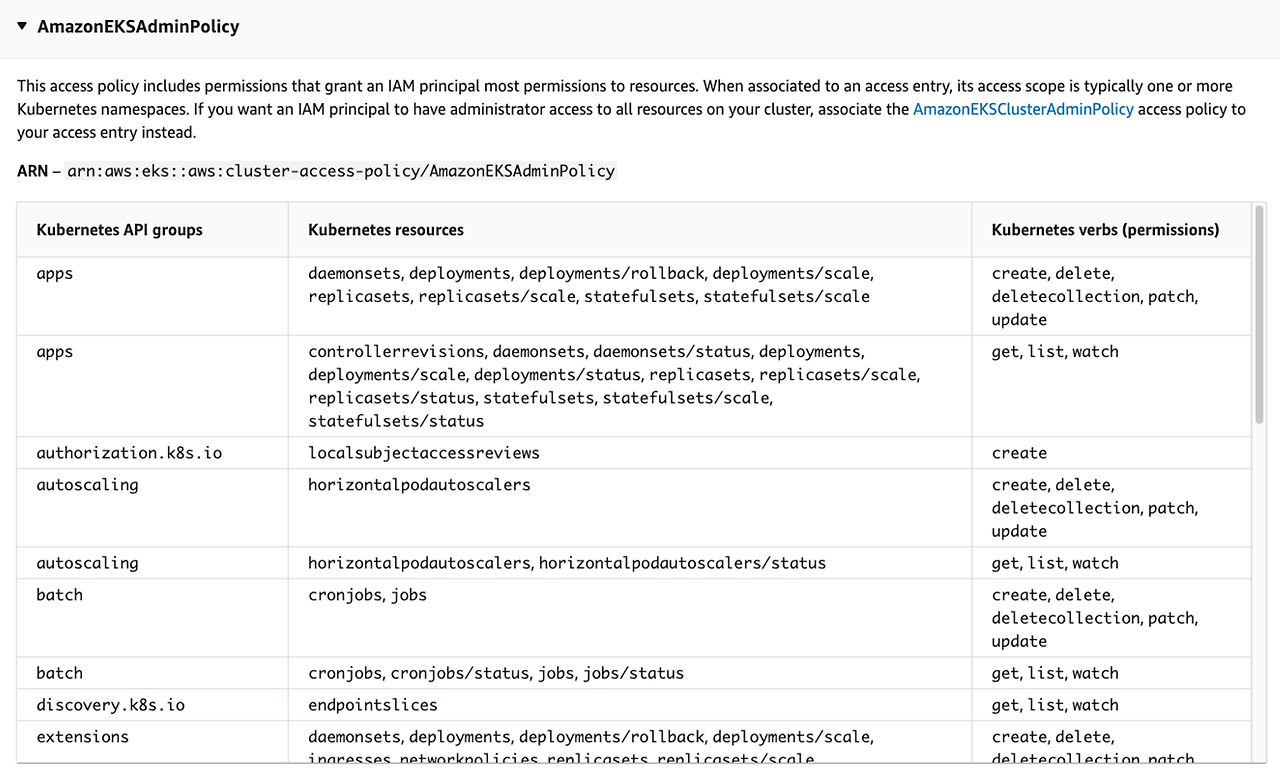
https://docs.aws.amazon.com/eks/latest/userguide/access-policies.html#access-policy-permissions # EKS API 액세스모드로 변경 aws eks update-cluster-config --name $CLUSTER_NAME --access-config authenticationMode=API
# List all access policies : 클러스터 액세스 관리를 위해 지원되는 액세스 정책 ## AmazonEKSClusterAdminPolicy – 클러스터 관리자 ## AmazonEKSAdminPolicy – 관리자 ## AmazonEKSEditPolicy – 편집 ## AmazonEKSViewPolicy – 보기 aws eks list-access-policies | jq
# 맵핑 클러스터롤 정보 확인 kubectl get clusterroles -l 'kubernetes.io/bootstrapping=rbac-defaults' | grep -v 'system:'
kubectl describe clusterroles admin kubectl describe clusterroles cluster-admin kubectl describe clusterroles edit kubectl describe clusterroles view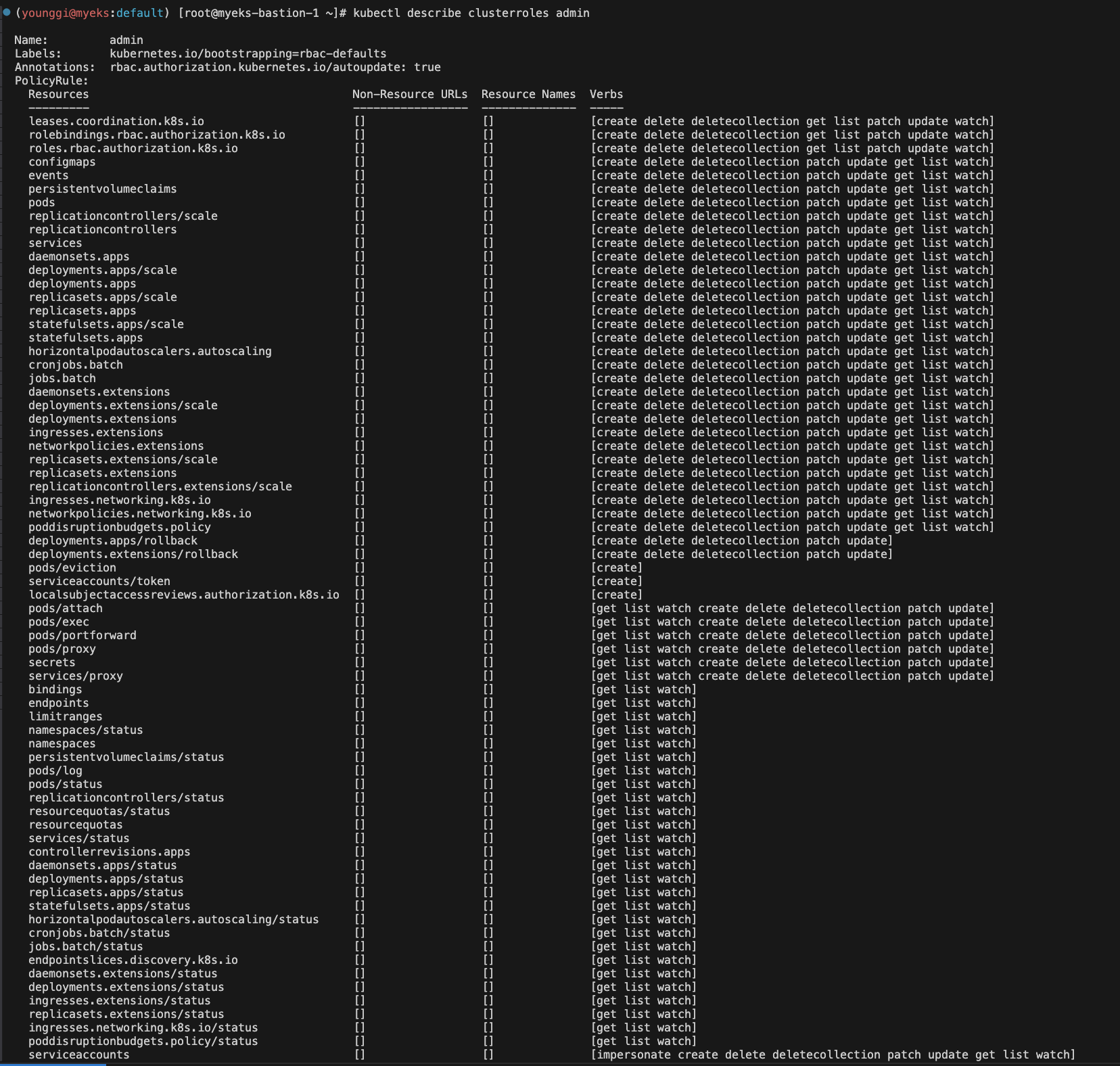
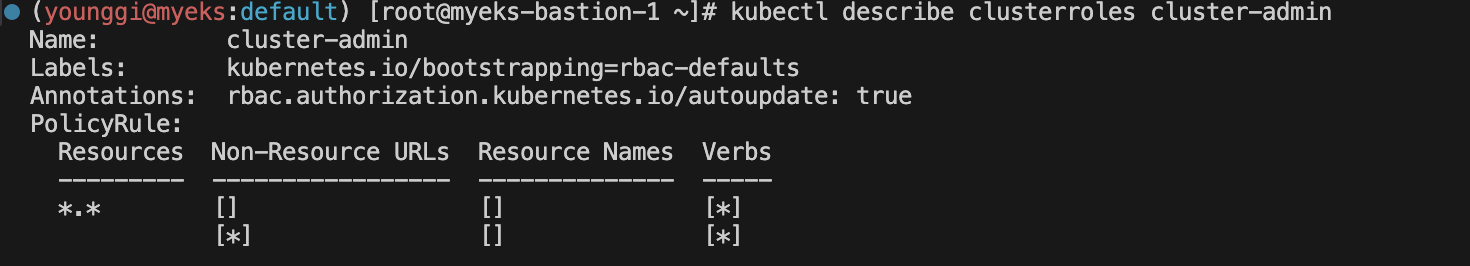
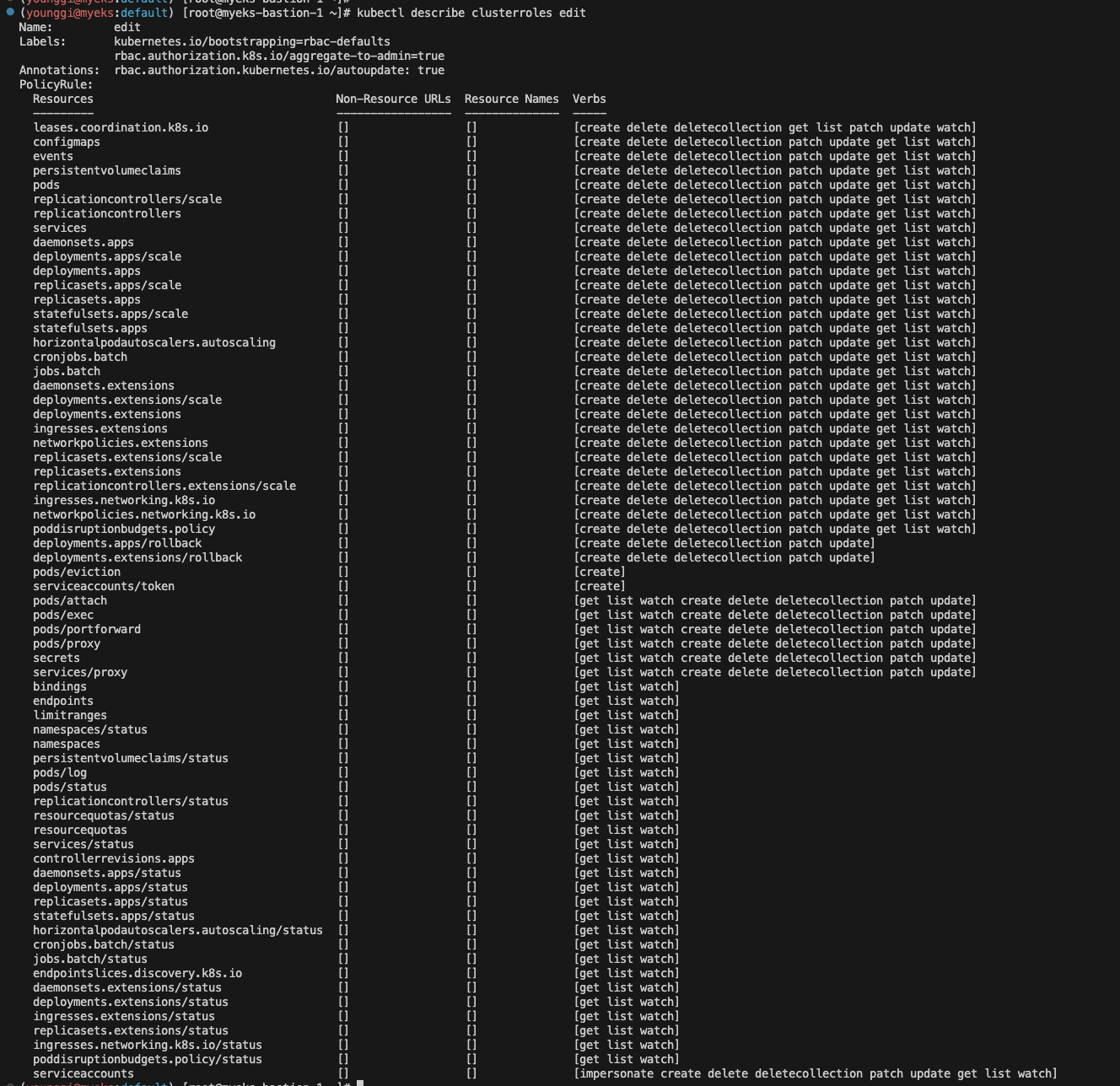
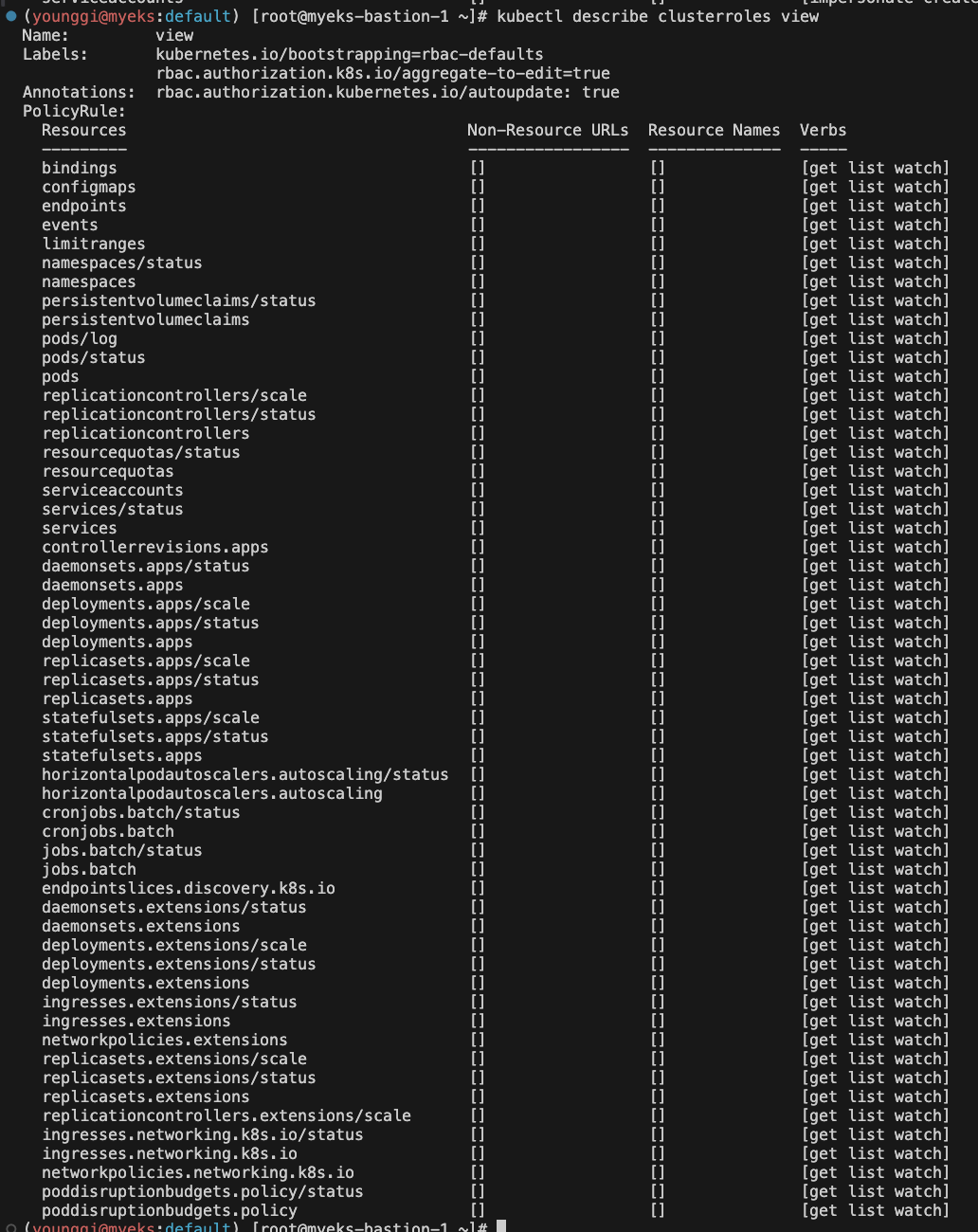
aws eks list-access-entries --cluster-name $CLUSTER_NAME | jq
aws eks list-associated-access-policies --cluster-name $CLUSTER_NAME --principal-arn arn:aws:iam::$ACCOUNT_ID:user/younggi | jq
aws eks list-associated-access-policies --cluster-name $CLUSTER_NAME --principal-arn arn:aws:iam::$ACCOUNT_ID:role/eksctl-myeks-nodegroup-ng1-NodeInstanceRole-R3LXCzM6urN2 | jq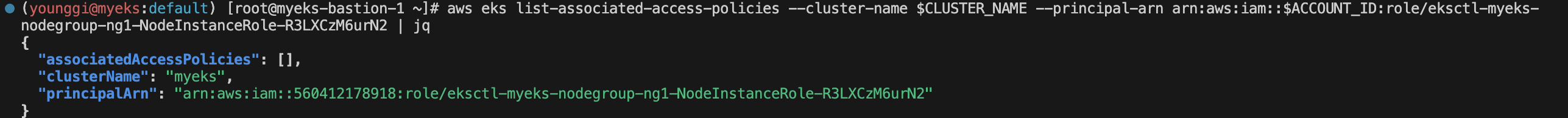
aws eks describe-access-entry --cluster-name $CLUSTER_NAME --principal-arn arn:aws:iam::$ACCOUNT_ID:user/younggi | jq
aws eks describe-access-entry --cluster-name $CLUSTER_NAME --principal-arn arn:aws:iam::$ACCOUNT_ID:role/eksctl-myeks-nodegroup-ng1-NodeInstanceRole-R3LXCzM6urN2 | jq
testuser 설정
# testuser 사용자 생성 aws iam create-user --user-name testuser# 사용자에게 프로그래밍 방식 액세스 권한 부여 aws iam create-access-key --user-name testuser# testuser 사용자에 정책을 추가 aws iam attach-user-policy --policy-arn arn:aws:iam::aws:policy/AdministratorAccess --user-name testuser# testuser 의 access entry 생성 **aws eks create-access-entry --cluster-name $CLUSTER_NAME --principal-arn arn:aws:iam::$ACCOUNT_ID:user/testuser**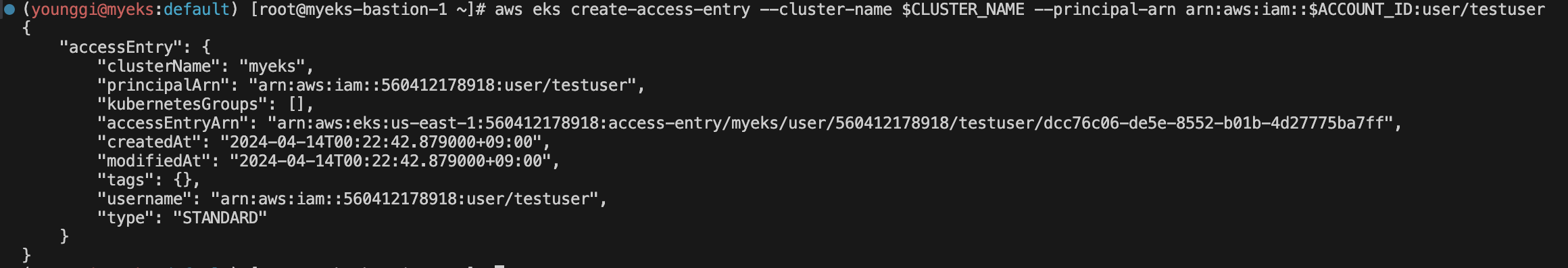
aws eks list-access-entries --cluster-name $CLUSTER_NAME | jq -r .accessEntries[]
# testuser에 AmazonEKSClusterAdminPolicy 연동 aws eks associate-access-policy --cluster-name $**CLUSTER_NAME** --principal-arn arn:aws:iam::$ACCOUNT_ID:user/**testuser \\** --policy-arn arn:aws:eks::aws:cluster-access-policy/**AmazonEKSClusterAdminPolicy** --access-scope type=**cluster**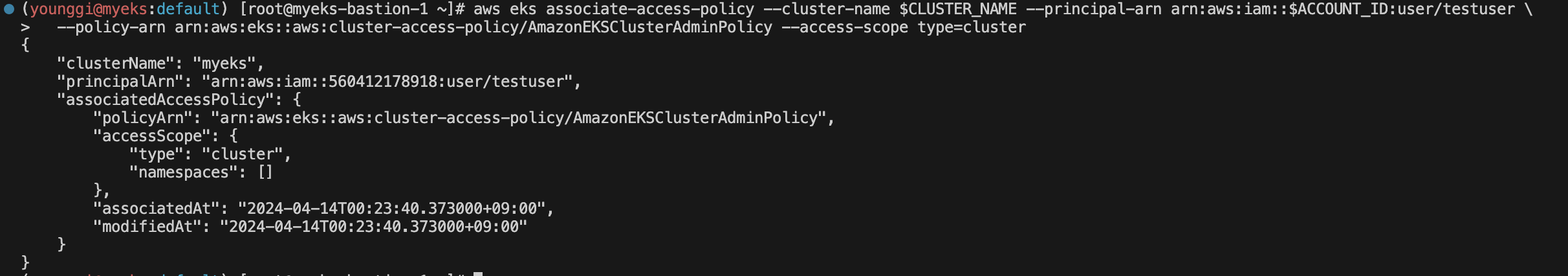
aws eks list-associated-access-policies --cluster-name $CLUSTER_NAME --principal-arn arn:aws:iam::$ACCOUNT_ID:user/testuser | jq aws eks describe-access-entry --cluster-name $CLUSTER_NAME --principal-arn arn:aws:iam::$ACCOUNT_ID:user/testuser | jq

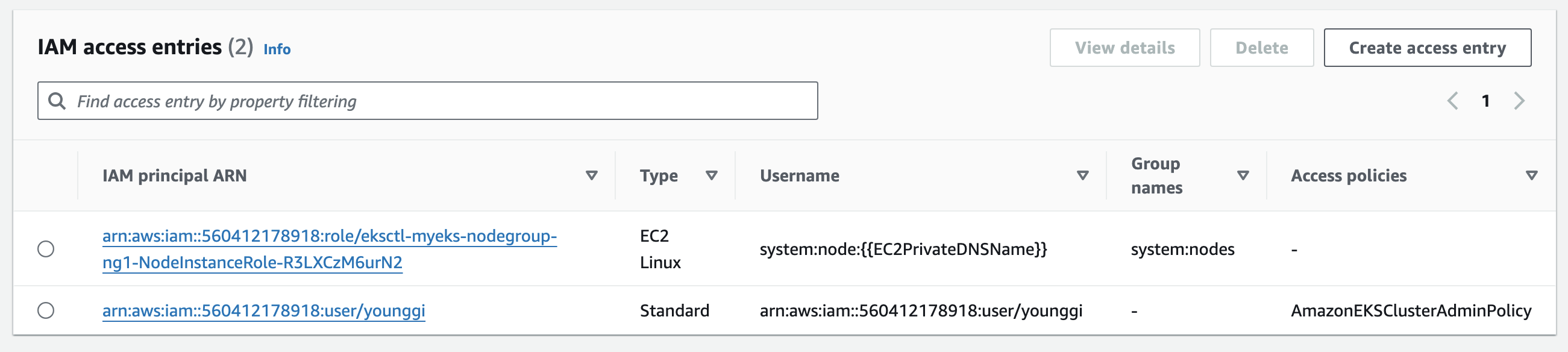
설정 전 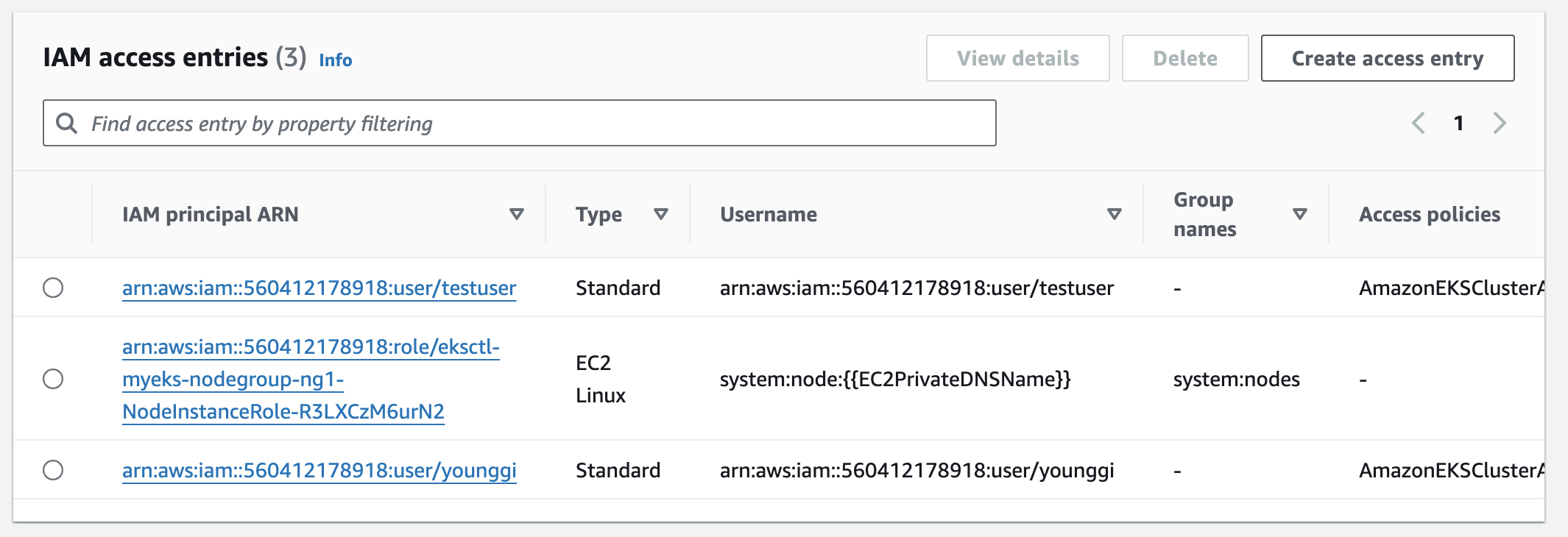
설정 후 [myeks-bastion-2]에서 testuser로 확인
# testuser 자격증명 설정 aws configure AWS Access Key ID [None]: *AKIA5ILF2F...* AWS Secret Access Key [None]: *ePpXdhA3cP....* Default region name [None]: *ap-northeast-2*# testuser 정보 확인 aws sts get-caller-identity --query Arn kubectl whoami # kubectl 시도 kubectl get node -v6 kubectl api-resources -v5 kubectl rbac-tool whoami kubectl auth can-i delete pods --all-namespaces kubectl get cm -n kube-system aws-auth -o yaml | kubectl neat | yh eksctl get iamidentitymapping --cluster $CLUSTER_NAME
aws sts get-caller-identity --query Arn 
kubectl whoami 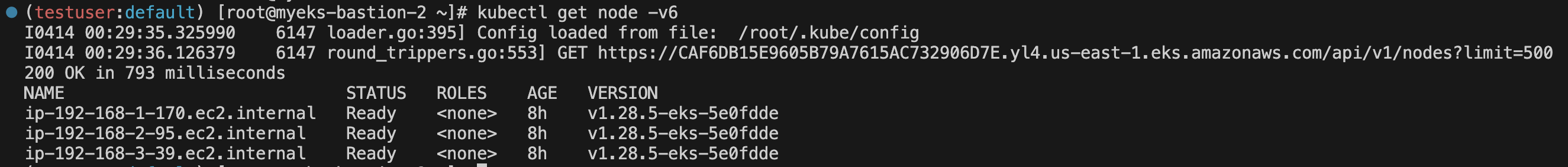
kubectl get node -v6 
kubectl api-resources -v5 
kubectl rbac-tool whoami 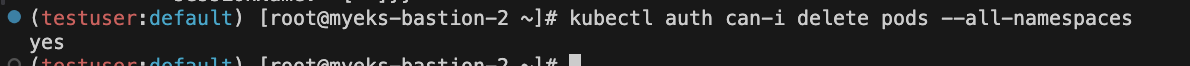
kubectl auth can-i delete pods --all-namespaces 
{"originWidth":1378,"originHeight":368,"style":"alignCenter","caption":"kubectl get cm -n kube-system aws-auth -o yaml 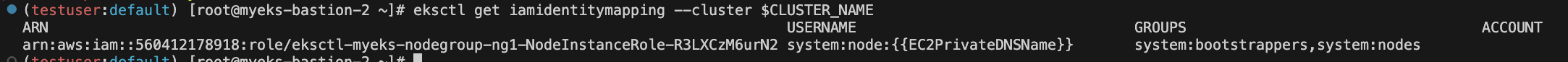
eksctl get iamidentitymapping --cluster $CLUSTER_NAME Access entries and Kubernetes groups
# 기존 testuser access entry 제거 aws eks delete-access-entry --cluster-name $CLUSTER_NAME --principal-arn arn:aws:iam::$ACCOUNT_ID:user/testuser aws eks list-access-entries --cluster-name $CLUSTER_NAME | jq -r .accessEntries[]
cat <<EoF> ~/pod-viewer-role.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: pod-viewer-role rules: - apiGroups: [""] resources: ["pods"] verbs: ["list", "get", "watch"] EoF
cat <<EoF> ~/pod-admin-role.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: pod-admin-role rules: - apiGroups: [""] resources: ["pods"] verbs: ["*"] EoF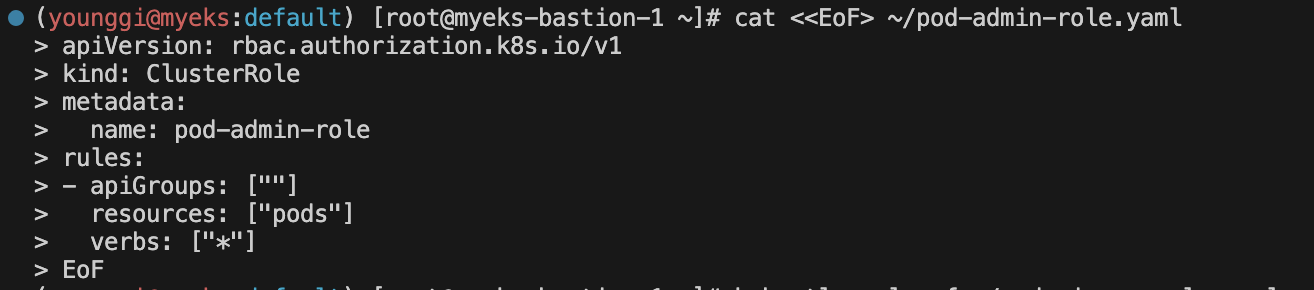
kubectl apply -f ~/pod-viewer-role.yaml kubectl apply -f ~/pod-admin-role.yaml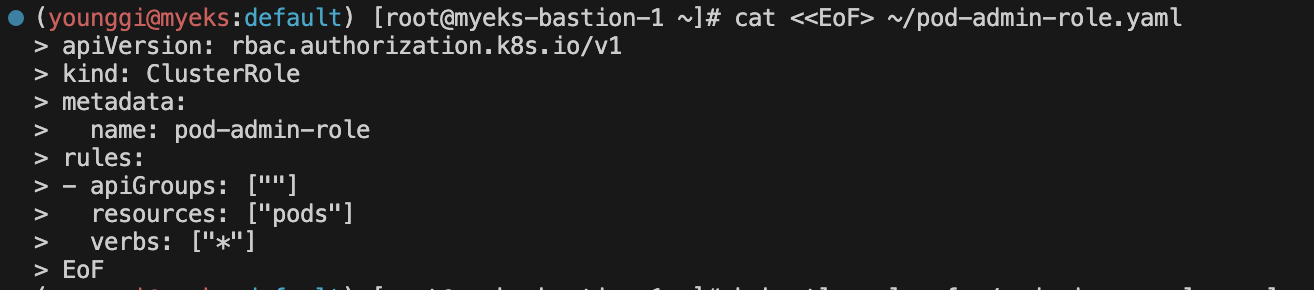
kubectl create clusterrolebinding viewer-role-binding --clusterrole=pod-viewer-role --group=pod-viewer kubectl create clusterrolebinding admin-role-binding --clusterrole=pod-admin-role --group=pod-admin

aws eks create-access-entry --cluster-name $CLUSTER_NAME --principal-arn arn:aws:iam::$ACCOUNT_ID:user/testuser --kubernetes-group pod-viewer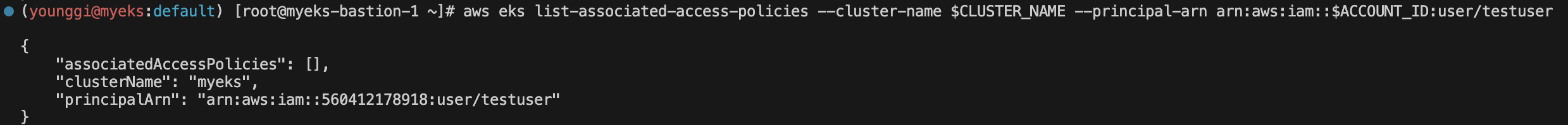
aws eks list-associated-access-policies --cluster-name $CLUSTER_NAME --principal-arn arn:aws:iam::$ACCOUNT_ID:user/testuser aws eks describe-access-entry --cluster-name $CLUSTER_NAME --principal-arn arn:aws:iam::$ACCOUNT_ID:user/testuser | jq
[myeks-bastion-2]에서 testuser로 확인
# testuser 정보 확인 aws sts get-caller-identity --query Arn kubectl whoami
# kubectl 시도 kubectl get pod -v6 kubectl api-resources -v5 kubectl auth can-i get pods --all-namespaces kubectl auth can-i delete pods --all-namespaces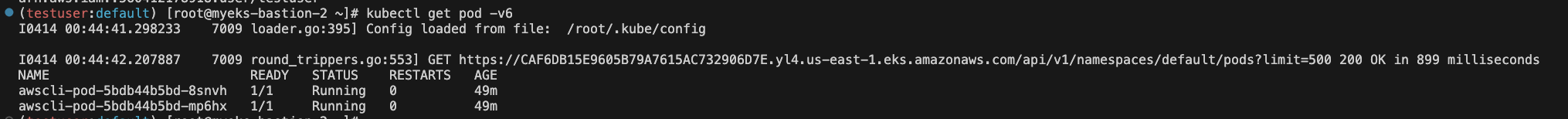
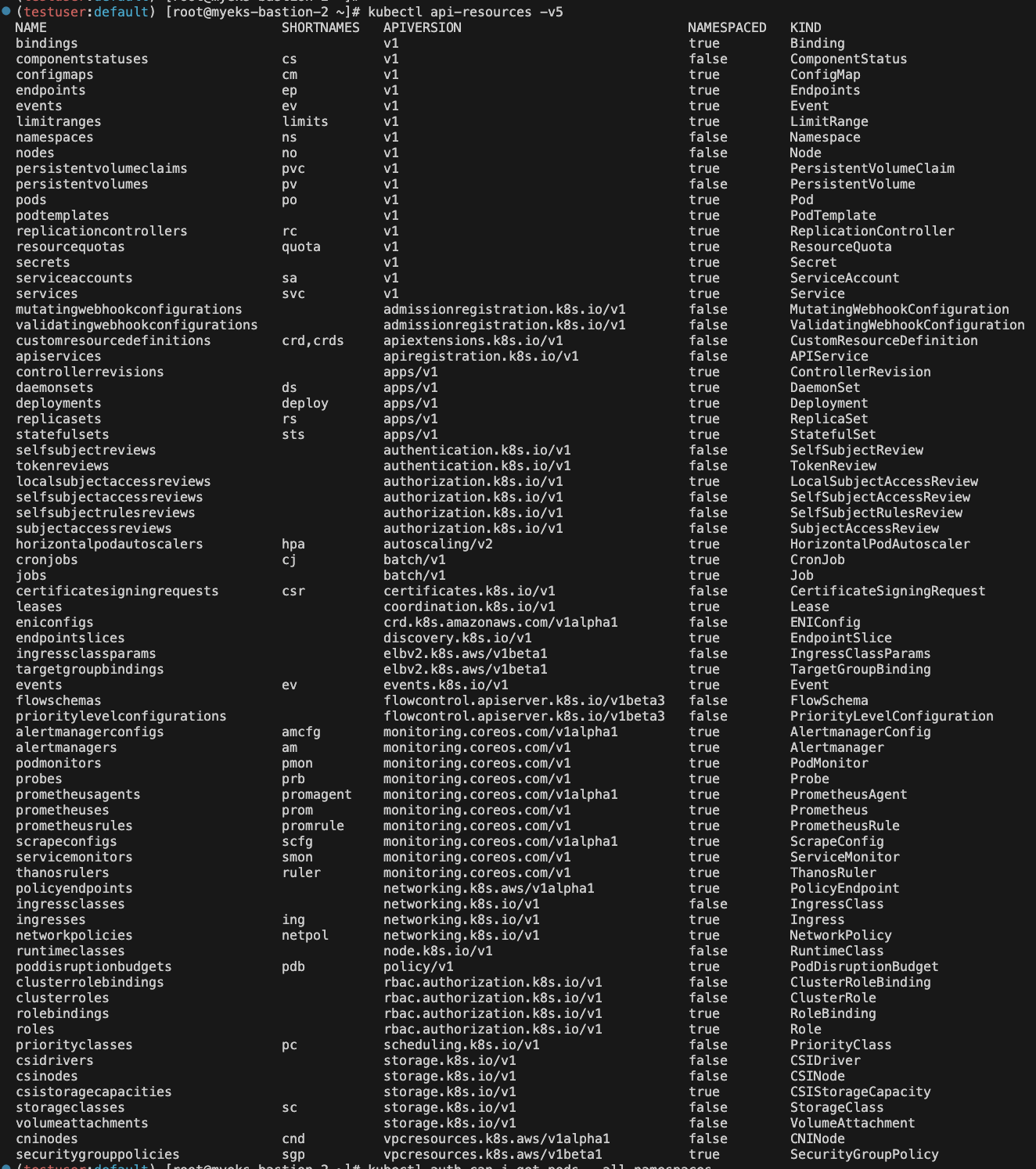
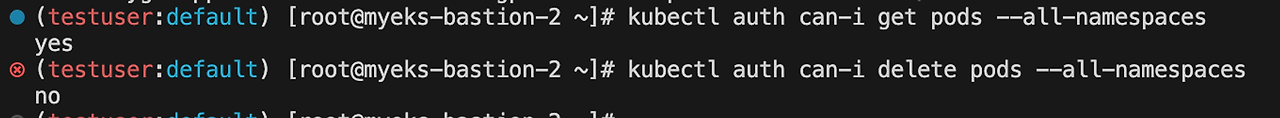
kubernetesGroups 업데이트 적용
aws eks update-access-entry --cluster-name $CLUSTER_NAME --principal-arn arn:aws:iam::$ACCOUNT_ID:user/testuser --kubernetes-group pod-admin | jq -r .accessEntryaws eks describe-access-entry --cluster-name $CLUSTER_NAME --principal-arn arn:aws:iam::$ACCOUNT_ID:user/testuser | jq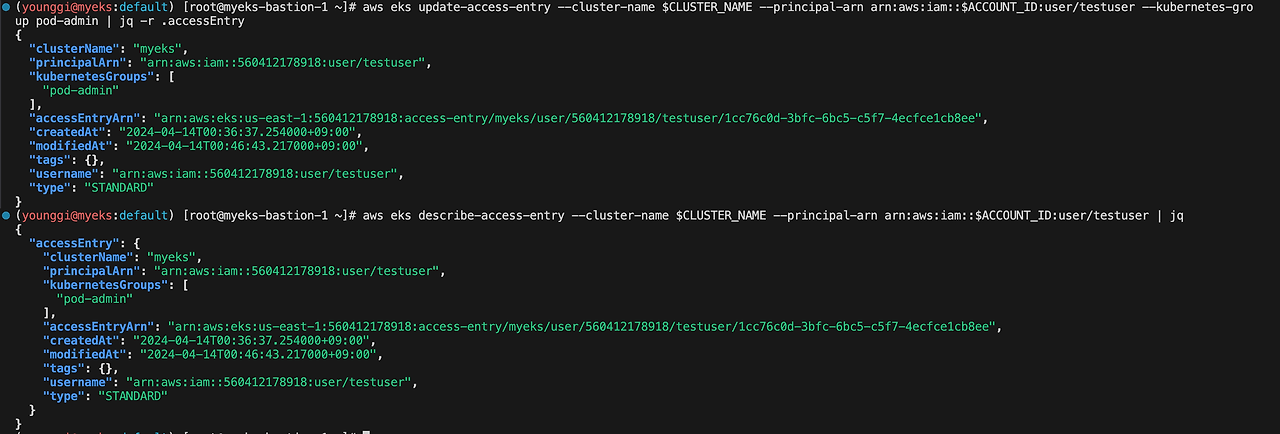
[myeks-bastion-2]에서 testuser로 확인
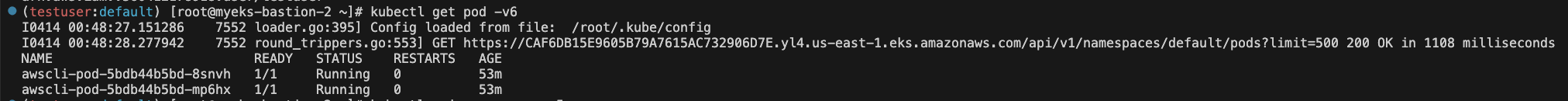
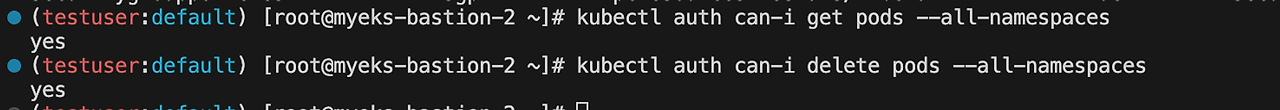
# testuser 정보 확인 aws sts get-caller-identity --query Arn kubectl whoami# kubectl 시도 kubectl get pod -v6 kubectl api-resources -v5 kubectl auth can-i get pods --all-namespaces kubectl auth can-i delete pods --all-namespaces
 다음글이전글이전 글이 없습니다.댓글
다음글이전글이전 글이 없습니다.댓글
스킨 업데이트 안내
현재 이용하고 계신 스킨의 버전보다 더 높은 최신 버전이 감지 되었습니다. 최신버전 스킨 파일을 다운로드 받을 수 있는 페이지로 이동하시겠습니까?
("아니오" 를 선택할 시 30일 동안 최신 버전이 감지되어도 모달 창이 표시되지 않습니다.)