AEWS2기
[실습] 2. EKS 인증/인가 - RBAC 관련 krew 플러그인
by yeongki0944
2024. 4. 13.
RBAC 관련 krew 플러그인 # 설치
kubectl krew install access-matrix rbac-tool rbac-view rolesum whoami
# k8s 인증된 주체 확인
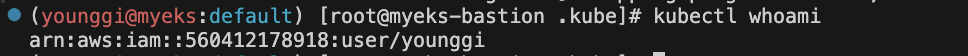
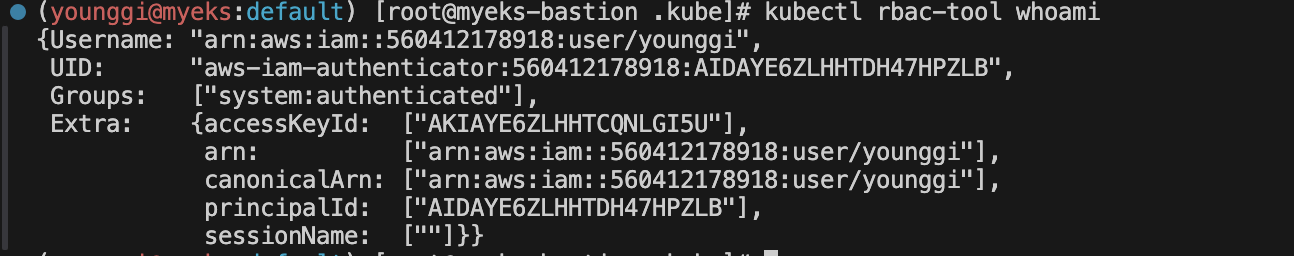
kubectl whoami
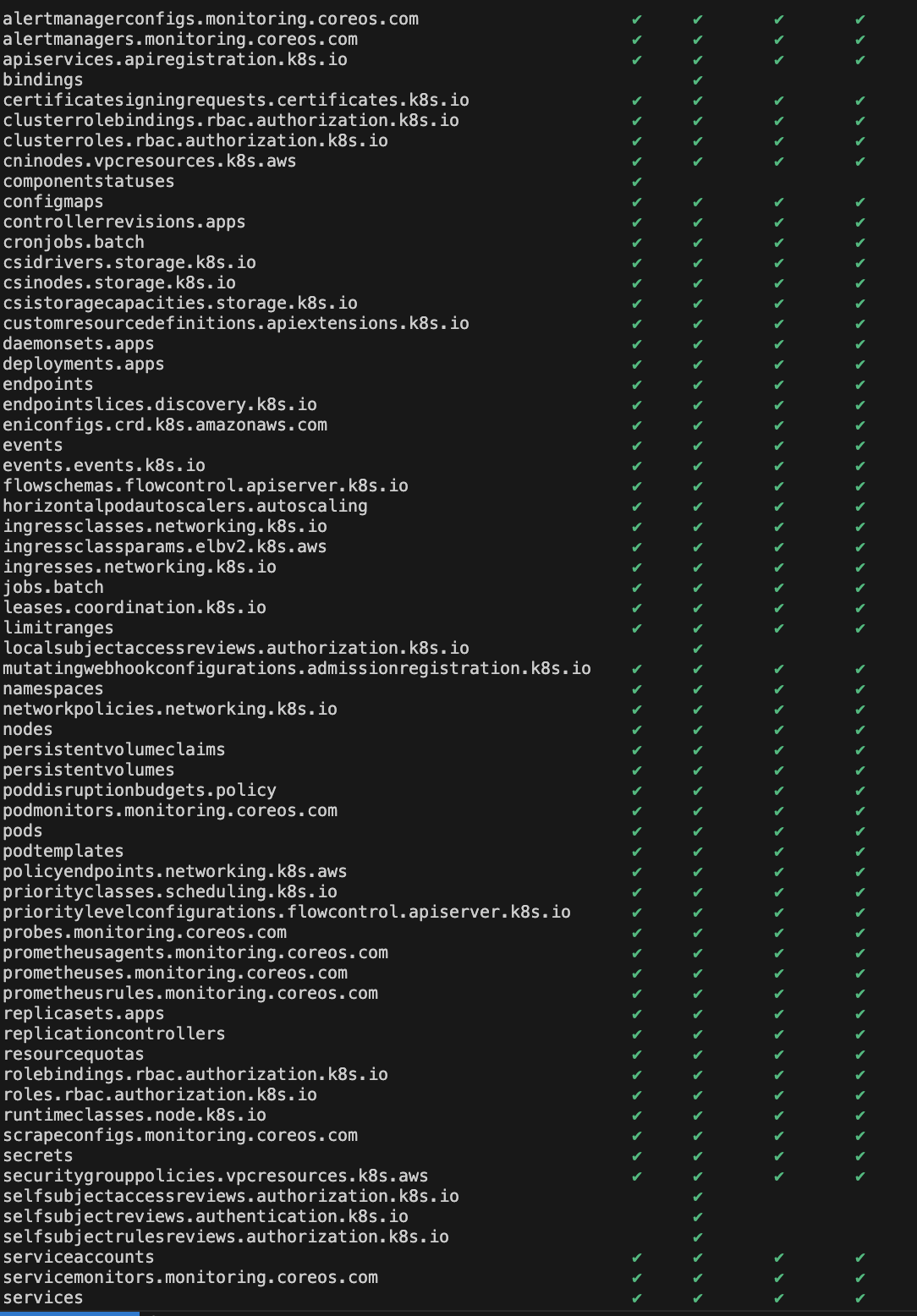
# Show an RBAC access matrix for server resources
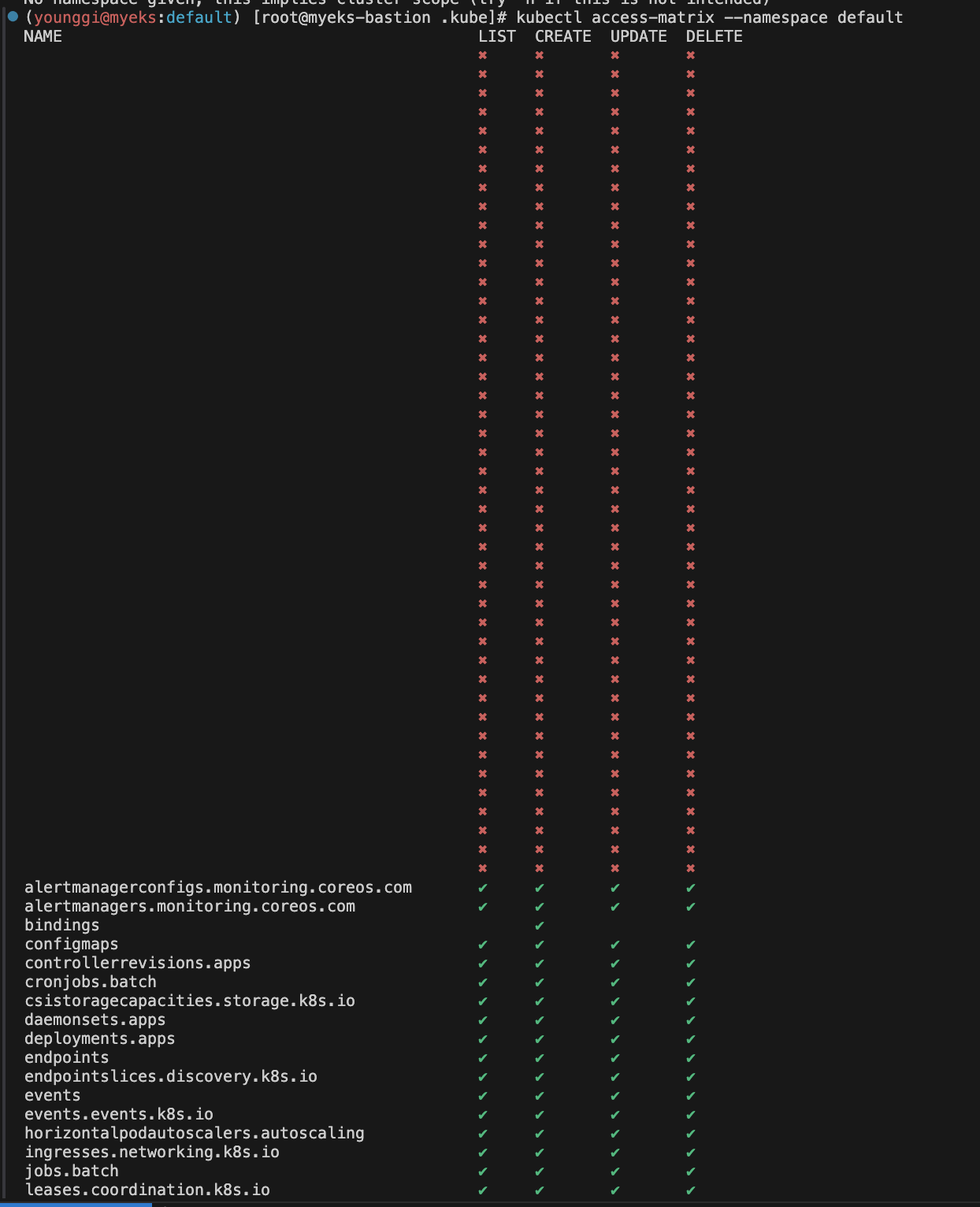
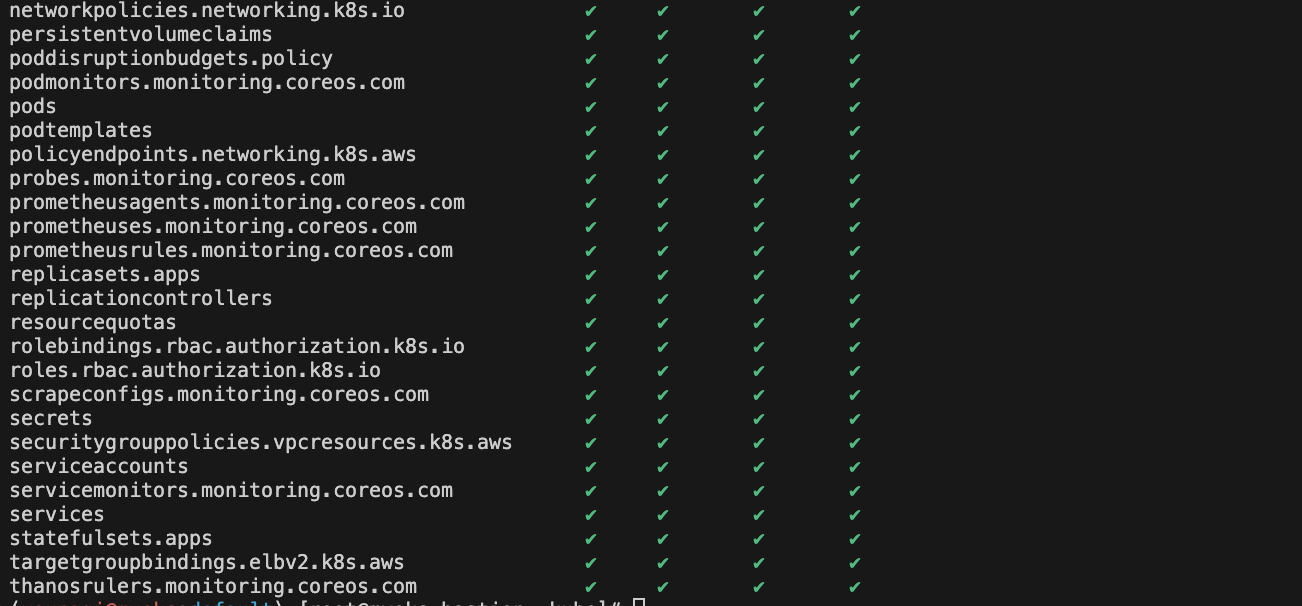
kubectl access-matrix # Review access to cluster-scoped resources
kubectl access-matrix --namespace default # Review access to namespaced resources in 'default'
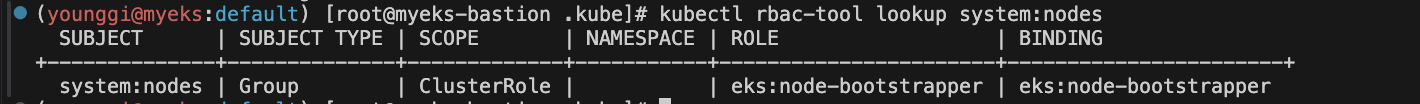
kubectl rbac-tool lookup system:nodes # eks:node-bootstrapper
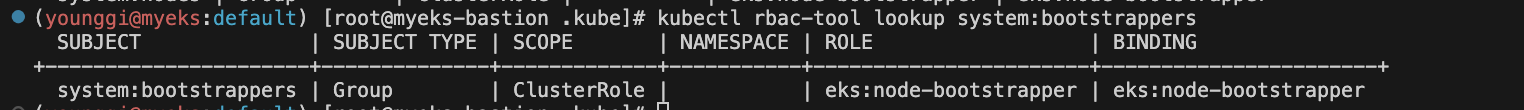
kubectl rbac-tool lookup system:bootstrappers # eks:node-bootstrapper
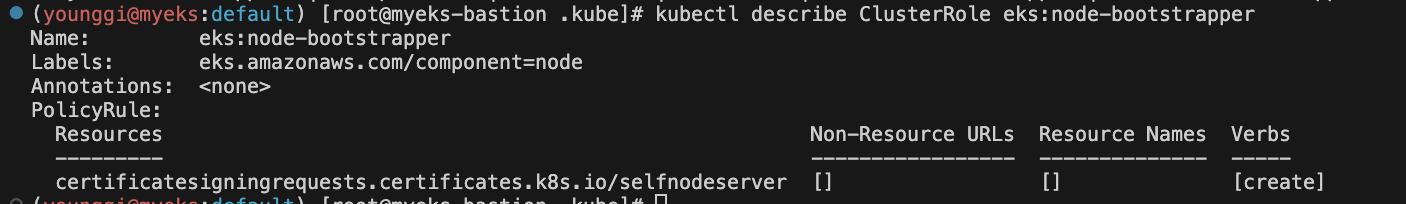
kubectl describe ClusterRole eks:node-bootstrapper
# RBAC List Policy Rules For subject (user/group/serviceaccount) name
kubectl rbac-tool policy-rules
kubectl rbac-tool policy-rules -e '^system:.*'
kubectl rbac-tool policy-rules -e '^system:authenticated'
# Generate ClusterRole with all available permissions from the target cluster
kubectl rbac-tool show
# Shows the subject for the current context with which one authenticates with the cluster
kubectl rbac-tool whoami
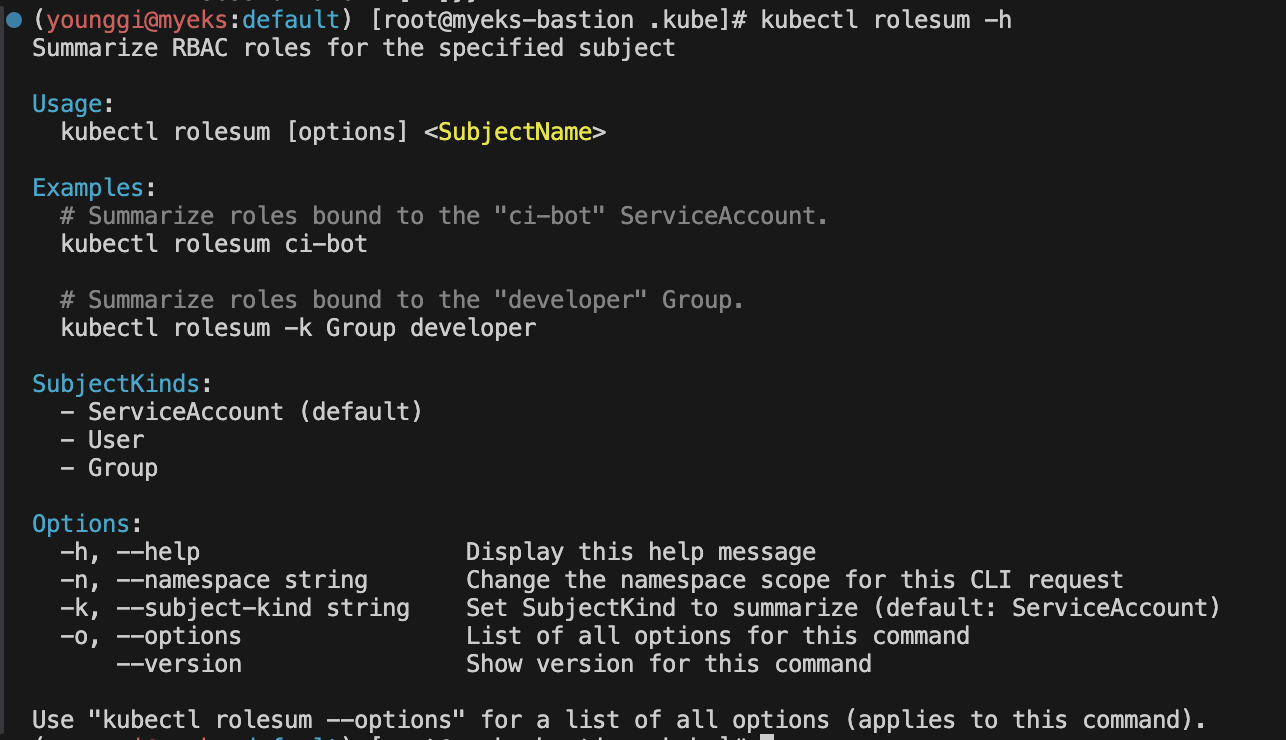
# Summarize RBAC roles for subjects : ServiceAccount(default), User, Group
kubectl rolesum -h
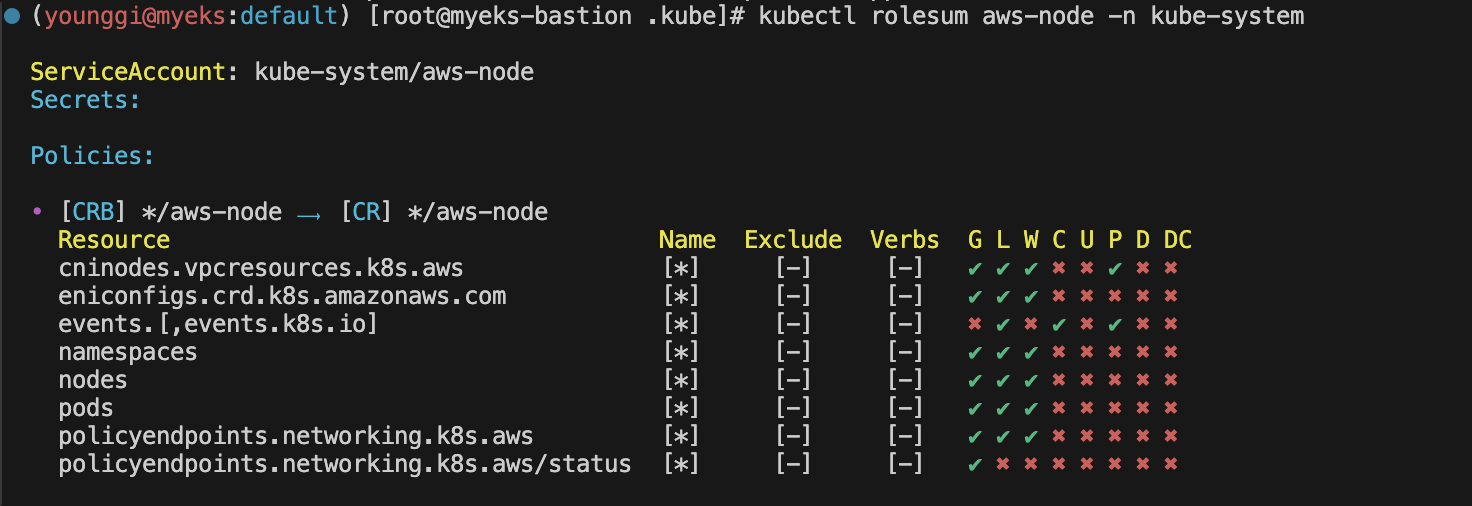
kubectl rolesum aws-node -n kube-system
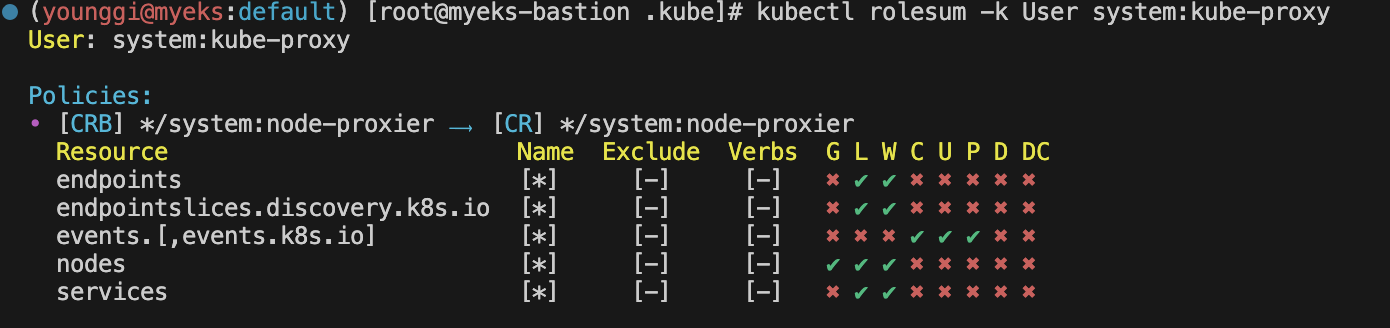
kubectl rolesum -k User system:kube-proxy
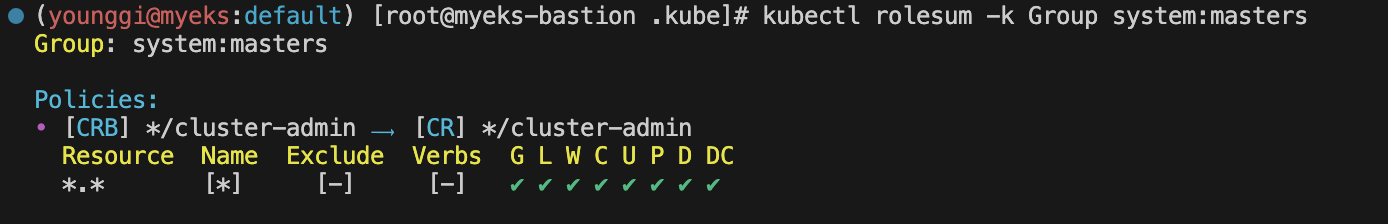
kubectl rolesum -k Group system:masters
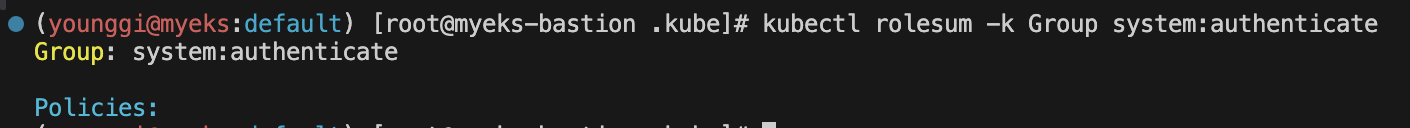
kubectl rolesum -k Group system:authenticate
# [터미널1] A tool to visualize your RBAC permissions
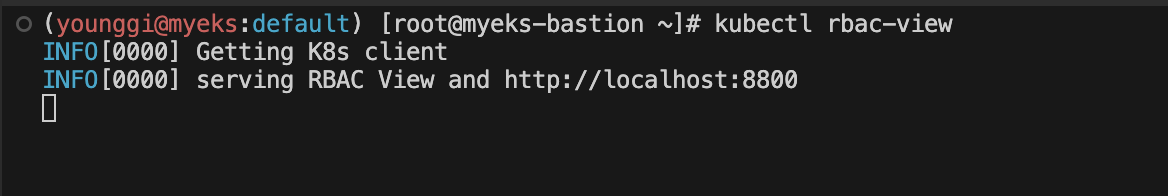
kubectl rbac-view
INFO[0000] Getting K8s client
INFO[0000] serving RBAC View and <http://localhost:8800>
## 이후 해당 작업용PC 공인 IP:8800 웹 접속 : 최초 접속 후 정보 가져오는데 다시 시간 걸림 (2~3분 정도 후 화면 출력됨)
echo -e "RBAC View Web <http://$>(curl -s ipinfo.io/ip):8800