1. 준비 사항
- GitHub 계정
- AWS 계정 (예제에서 AWS 리소스를 생성할 예정)
- 로컬 머신 또는 EC2 인스턴스 (Atlantis 서버 실행용)
2. GitHub 리포지토리
리포지토리 생성

Token 생성
Github → Settings → Developer settings ⇒ Personal access tokens : Tokens (classic) ← Repo 제한 가능 Fine-grained tokens 사용 권장

https://github.com/terraform-aws-modules/terraform-aws-atlantis
GitHub - terraform-aws-modules/terraform-aws-atlantis: Terraform module to deploy Atlantis on AWS Fargate 🇺🇦
Terraform module to deploy Atlantis on AWS Fargate 🇺🇦 - terraform-aws-modules/terraform-aws-atlantis
github.com
Route53 설정 false로 변경
variable "create" {
description = "Determines whether resources will be created (affects all resources)"
type = bool
default = true
}
variable "tags" {
description = "A map of tags to add to all resources"
type = map(string)
default = {}
}
################################################################################
# Cluster
################################################################################
variable "cluster_name" {
description = "Name of the cluster (up to 255 letters, numbers, hyphens, and underscores)"
type = string
default = ""
}
variable "cluster_configuration" {
description = "The execute command configuration for the cluster"
type = any
default = {}
}
variable "cluster_settings" {
description = "List of configuration block(s) with cluster settings. For example, this can be used to enable CloudWatch Container Insights for a cluster"
type = any
default = [
{
name = "containerInsights"
value = "enabled"
}
]
}
variable "cluster_service_connect_defaults" {
description = "Configures a default Service Connect namespace"
type = map(string)
default = {}
}
variable "cluster_tags" {
description = "A map of additional tags to add to the cluster"
type = map(string)
default = {}
}
################################################################################
# CloudWatch Log Group
################################################################################
variable "create_cloudwatch_log_group" {
description = "Determines whether a log group is created by this module for the cluster logs. If not, AWS will automatically create one if logging is enabled"
type = bool
default = true
}
variable "cloudwatch_log_group_name" {
description = "Custom name of CloudWatch Log Group for ECS cluster"
type = string
default = null
}
variable "cloudwatch_log_group_retention_in_days" {
description = "Number of days to retain log events"
type = number
default = 90
}
variable "cloudwatch_log_group_kms_key_id" {
description = "If a KMS Key ARN is set, this key will be used to encrypt the corresponding log group. Please be sure that the KMS Key has an appropriate key policy (https://docs.aws.amazon.com/AmazonCloudWatch/latest/logs/encrypt-log-data-kms.html)"
type = string
default = null
}
variable "cloudwatch_log_group_tags" {
description = "A map of additional tags to add to the log group created"
type = map(string)
default = {}
}
################################################################################
# Capacity Providers
################################################################################
variable "default_capacity_provider_use_fargate" {
description = "Determines whether to use Fargate or autoscaling for default capacity provider strategy"
type = bool
default = true
}
variable "fargate_capacity_providers" {
description = "Map of Fargate capacity provider definitions to use for the cluster"
type = any
default = {}
}
variable "autoscaling_capacity_providers" {
description = "Map of autoscaling capacity provider definitions to create for the cluster"
type = any
default = {}
}
################################################################################
# Task Execution - IAM Role
# https://docs.aws.amazon.com/AmazonECS/latest/developerguide/task_execution_IAM_role.html
################################################################################
variable "create_task_exec_iam_role" {
description = "Determines whether the ECS task definition IAM role should be created"
type = bool
default = false
}
variable "task_exec_iam_role_name" {
description = "Name to use on IAM role created"
type = string
default = null
}
variable "task_exec_iam_role_use_name_prefix" {
description = "Determines whether the IAM role name (`task_exec_iam_role_name`) is used as a prefix"
type = bool
default = true
}
variable "task_exec_iam_role_path" {
description = "IAM role path"
type = string
default = null
}
variable "task_exec_iam_role_description" {
description = "Description of the role"
type = string
default = null
}
variable "task_exec_iam_role_permissions_boundary" {
description = "ARN of the policy that is used to set the permissions boundary for the IAM role"
type = string
default = null
}
variable "task_exec_iam_role_tags" {
description = "A map of additional tags to add to the IAM role created"
type = map(string)
default = {}
}
variable "task_exec_iam_role_policies" {
description = "Map of IAM role policy ARNs to attach to the IAM role"
type = map(string)
default = {}
}
variable "create_task_exec_policy" {
description = "Determines whether the ECS task definition IAM policy should be created. This includes permissions included in AmazonECSTaskExecutionRolePolicy as well as access to secrets and SSM parameters"
type = bool
default = true
}
variable "task_exec_ssm_param_arns" {
description = "List of SSM parameter ARNs the task execution role will be permitted to get/read"
type = list(string)
default = ["arn:aws:ssm:*:*:parameter/*"]
}
variable "task_exec_secret_arns" {
description = "List of SecretsManager secret ARNs the task execution role will be permitted to get/read"
type = list(string)
default = ["arn:aws:secretsmanager:*:*:secret:*"]
}
variable "task_exec_iam_statements" {
description = "A map of IAM policy [statements](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/data-sources/iam_policy_document#statement) for custom permission usage"
type = any
default = {}
}
################################################################################
# Service(s)
################################################################################
variable "services" {
description = "Map of service definitions to create"
type = any
default = {}
}
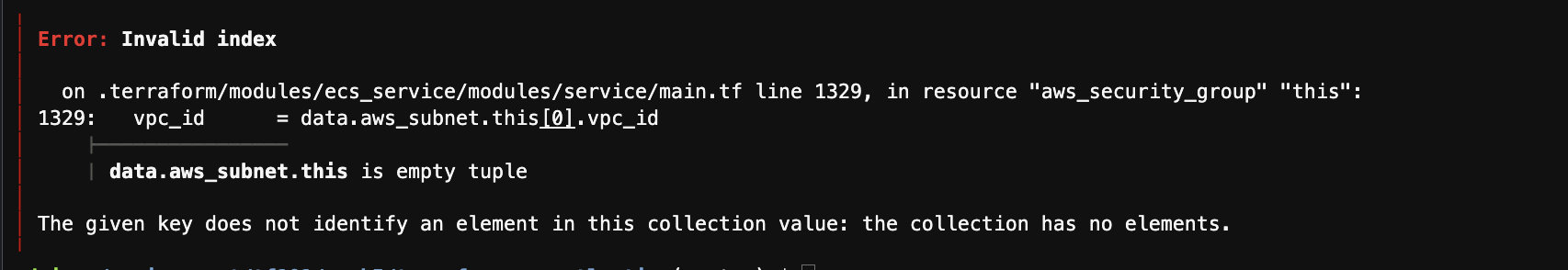
현재 아래 이슈 해결중